~ 2 min read
Avoid The Node.js Security Storm


Keeping your 3rd party project dependencies secured is such an important task that you can’t under-estimate.
Snyk is a great tool for monitoring and tracking security vulnerabilities within your Node.js dependencies (and their dependencies).
It’s a stand-alone tool, a platform, and also an active community of security researchers who provide you with patches to insecure code until an upstream package will get an update. This is extremely valuable as you don’t have to wait until an update is made to a package, or just if you don’t want to upgrade to new, possibly breaking features, and get patched the security hole.
Test for Vulnerabilities
Install snyk as a global dependency so you can set it to monitor your project through snyk’s own dashboard.
Installing snyk:
npm install -i snykNext up, running snyk test in your project will check all dependencies in your project:
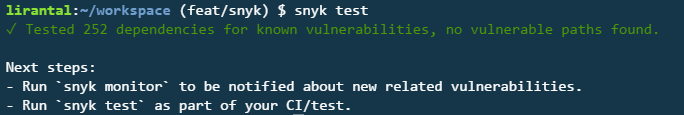
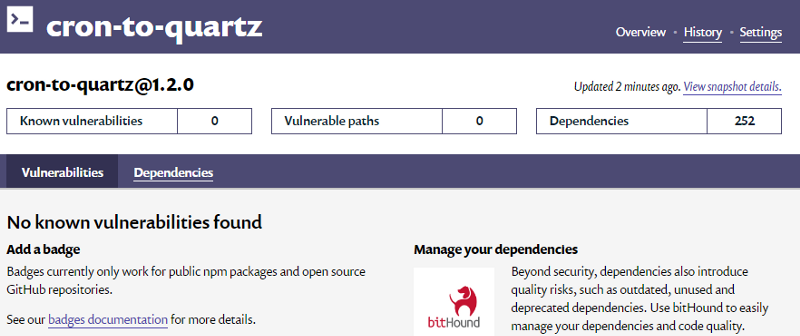
Luckily I don’t have any vulnerabilities :-)
Monitoring your GitHub projects
Login to your snyk.io account and browse to the Projects area.
There you should locate a Test my GitHub repositories button on the right side, just click it:
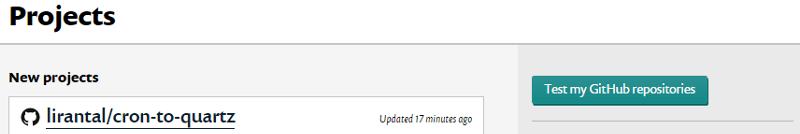
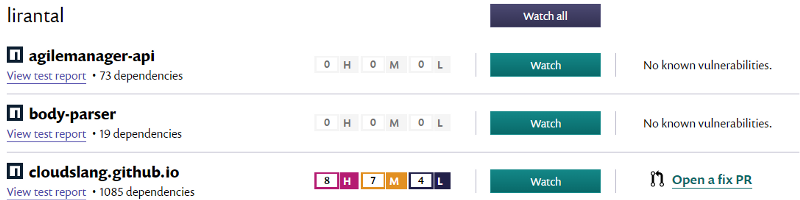
Your GitHub repositories will then show up and you can click on the Watch button to start tracking them, getting notifications on insecure vulnerabilities found there:
Monitoring your project from the CLI
This is useful as you track the project with every change that happens, get notifications, etc.
All monitoring added from the CLI will automatically show up as private projects in your account’s dashboard.
Authenticate to snyk.io so you can track your package:
snyk auth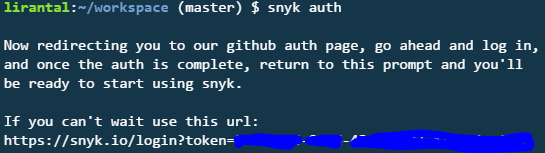
Now to monitor and track the project dependencies run:
snyk monitorThen you can view it in the dashboard as one of your projects at: https://snyk.io
CI/CD Integration
Installing snyk for the build:
before_install:
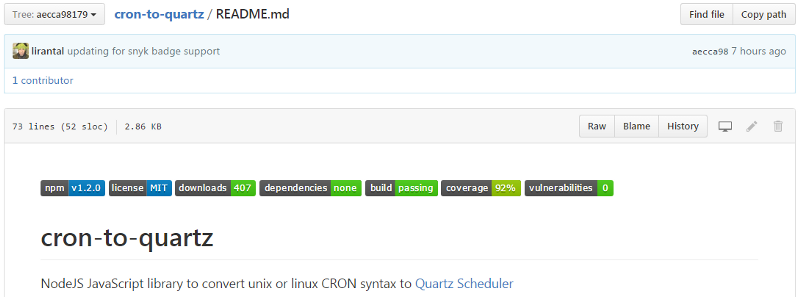
- npm install snyk -gIt’s great to also add a badge to your README file so that quality is visible to anyone who explores the project in GitHub or npmjs.com.
Modify the following markdown to match your project’s GitHub’s USER and repo REPONAME:
Here’s how it looks like in my own project —
it’s the last badge specifying 0 vulnerabilities.
Also, I invite you to read my newly published book Essential Node.js Security

