~ 3 min read
Secure Your MCP Servers with Environment Variable Risk Assessment
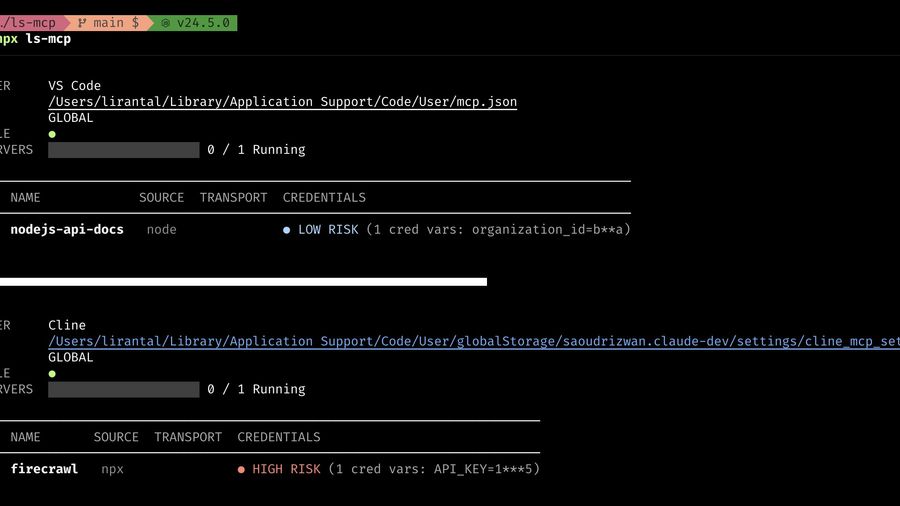
The latest update to the ls-mcp tool introduces a crucial security feature: the ability to detect and assess the risk level of credentials stored in environment variables within MCP server configurations. This enhancement helps developers and security teams identify potential security risks by flagging high-risk credentials such as API keys and tokens. By integrating this feature, users can better secure their AI application environments and ensure compliance with security standards.
Prerequisites
Before diving into the new feature, ensure you have the following:
- Node.js: Current LTS version
- npm: Installed and configured
- Access: A system with MCP server configurations
Understand the Problem
Environment variables are a common method for storing sensitive information like API keys and tokens. However, they pose a security risk if not managed properly. The ls-mcp tool now includes a feature to detect and categorize these risks, helping you secure your MCP server configurations.
Feature Overview: Credential Risk Detection
The new credential risk detection feature in ls-mcp is designed to identify and categorize potential security risks in environment variables. This feature scans MCP server configurations for common patterns in environment variable names that suggest sensitive information, such as API_KEY or SECRET_TOKEN.
Why This Matters
Identifying and categorizing credential risks is crucial for maintaining the security of your AI applications. By flagging high-risk credentials, you can take proactive measures to secure your environment and comply with security standards.
How It Works
The tool uses pattern matching and heuristics to detect environment variables that likely contain sensitive information. It then categorizes these variables based on their risk level, providing a clear indication of potential security threats.
Technical Implementation
Credential Detection Service
The credential detection service is the core of this new feature. It uses pattern matching to identify environment variables that may contain sensitive information. Common patterns include names like API_KEY, SECRET, and TOKEN.
{
"mcpServers": {
"firecrawl-mcp": {
"command": "npx",
"args": ["-y", "firecrawl-mcp"],
"transport": "stdio",
"env": {
"FIRECRAWL_API_KEY": "12345"
}
}
}
}Why this matters: This example demonstrates how sensitive information is detected and flagged.
Verify: Run the ls-mcp tool and observe the CLI output for risk indicators.
Integration with MCP Config Parser
The credential detection feature is seamlessly integrated into the existing MCP config parser. This integration ensures that the detection process is part of the standard workflow, providing continuous security monitoring.
Render Service Updates
The CLI output has been updated to include visual indicators of risk levels. This enhancement allows users to quickly assess the security status of their environment variables.
Conclusion
The new credential risk detection feature in ls-mcp is a significant step forward in securing MCP server configurations. By identifying and categorizing potential security risks, this feature helps you protect your AI applications and comply with security standards.
- Try the new feature by updating ls-mcp and running it on your configurations.
- Follow on X/Twitter for new guides and security research.
- Explore more code examples and related work on GitHub.
Follow on X/Twitter for updates and new guides.
Explore more code examples and related work on GitHub.
