~ 3 min read
The Uprising of Model Context Protocol (MCP) Security Research

Any time in technology history where a new technology emerges, quickly followed is a wave of security research. This is the good old cat and mouse game of security research. As new paradigms, tools, or protocols are introduced, vulnerabilities and various security issues are inevitably discovered, leading to patches, updates, and sometimes even new security frameworks. The Model Context Protocol (MCP) is no exception to this trend.
What is MCP?
The Model Context Protocol (MCP) is a protocol designed to facilitate the exchange of context information between AI models and applications. It aims to standardize how context is shared, ensuring that models can operate more effectively by understanding the environment in which they are deployed. MCP is particularly relevant in scenarios where AI models need to adapt to different contexts, such as varying user preferences, environmental conditions, or operational constraints.
The S in MCP: Security
Security is a critical aspect of any protocol, especially one that deals with AI models and their interactions with applications.
The Model Context Protocol (MCP) is a relatively young schematics that has been put forward by Anthropic only at the end of 2024, in November. As such, it was still in its infancy for many months and have lacked any wide adoption or security scrutiny. However, that changed very quickly in early 2025 at around March, when new MCP Servers were announced, and MCP clients like Cursor, Claude Desktop and others started to include integrations.
Security in MCP has initially been interpreted by consumers (developers and companies) as identity and access management, meaning authentication and authorization. While these are important security aspects to address in the protocol, they are not the only ones. As MCP adoption grew, so did the interest from security researchers to explore the protocol for potential vulnerabilities and security issues.
Security research for MCP, aside from identity, roles and permissions, extends to various areas, including:
- Supply chain security and malware: Ensuring that MCP implementations are free from malicious code and vulnerabilities that could be exploited by attackers. Malicious MCP Servers could not just have malicious code but also expose malicious tools via an attack known as Tool Poisoning.
- Insecure code: MCP servers may have insecure code that could lead to vulnerabilities such as command injection, path traversal, SSRF or other types of security issues.
Insecure MCP Servers
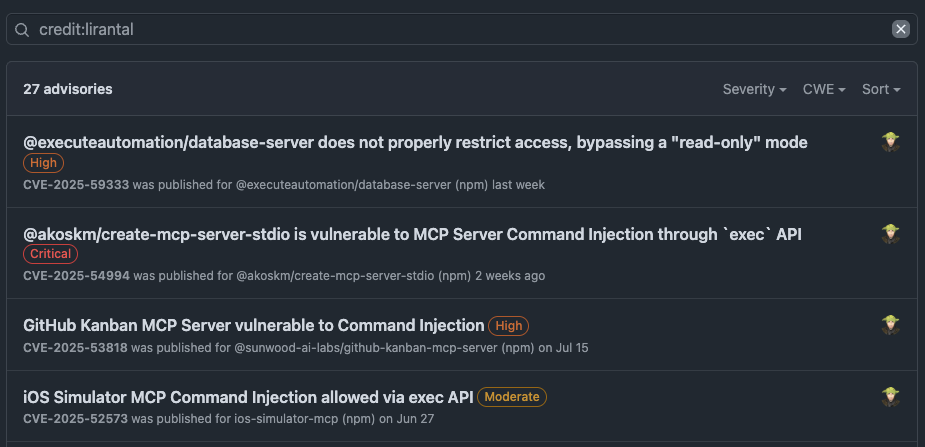
Exploring further the concept of flawed MCP Servers that unfortunately exist in the wild, there’s plenty of evidence that shows many MCP servers are insecure.
I’ve personally been researching the security of MCP Servers and have found dozen of them to be insecure. Some call-outs for published advisories that I can share include the following:
Which Security Vulnerabilities are Found in MCP Servers?
Security research from equixly finds that top security vulnerability types in MCP Servers include Command Injection, Path Traversal and SSRF types of vulnerabilities.
In correlation, I’ve authored three Node.js Secure Coding book, two of which focus on exactly these types of vulnerabilities, and I can confirm that these are the most common security issues in Node.js applications, which is the language of choice for many MCP Server implementations:
- Node.js Secure Coding: Defending Against Command Injection Vulnerabilities - Command Injection vulnerabilities
- Node.js Secure Coding: Prevention and Exploitation of Path Traversal Vulnerabilities - Path Traversal vulnerabilities
Vulnerabilities Deserves their Punny names and Logos
It is inevitable for security vulnerabilities to get punny names and logos. MCP vulnerabilities are no exception. So, for that, I’ve created the following visuals that I imagine will be circulating in the security community in the near future:

there’s also this one if you fancy a different flavor:

